Category Archives: Mac
Deciphering the searchpartyd macOS process and its impacts
The searchpartyd process in macOS is an integral part of Apple’s innovative location tracking system, introduced with macOS 10.15 Catalina, iOS 13, and iPadOS 13.1. This daemon is a cornerstone of the Find My service, enabling users to locate their devices, even when offline. Understanding searchpartyd, its functionality, and addressing common issues like high CPU usage is crucial for macOS users.
The Integral role and functionality of searchpartyd
At its core, searchpartyd serves as a major daemon within the Offline Finding (OF) system of the Find My app. Its primary function is to generate the necessary cryptographic keys and perform all related cryptographic operations. This process is vital for synchronizing keys, sending location reports as a finder device, and obtaining location reports for devices owned by the user.
When a device equipped with the Find My feature is lost, it emits Bluetooth Low Energy (BLE) signals containing a public key. These signals are picked up by finder devices, which then use the key to encrypt the location of the lost device and send this information back to Apple’s servers. The Find My app accesses these reports to help users locate their missing devices.
The dual nature of searchpartyd process
Although the authentic searchpartyd process is an integral component of macOS’s security and geolocation functionalities, it is crucial for users to remain vigilant against potentially intrusive programs (PIPs) that could disguise themselves with analogous nomenclature. Such deceptive applications have the capability to alter web browser configurations, leading to unwarranted redirects and the proliferation of diverse forms of online advertisements. This activity not only disrupts user experience but also contributes to a noticeable reduction in the Mac’s operational efficiency.
Addressing high CPU usage and management concerns
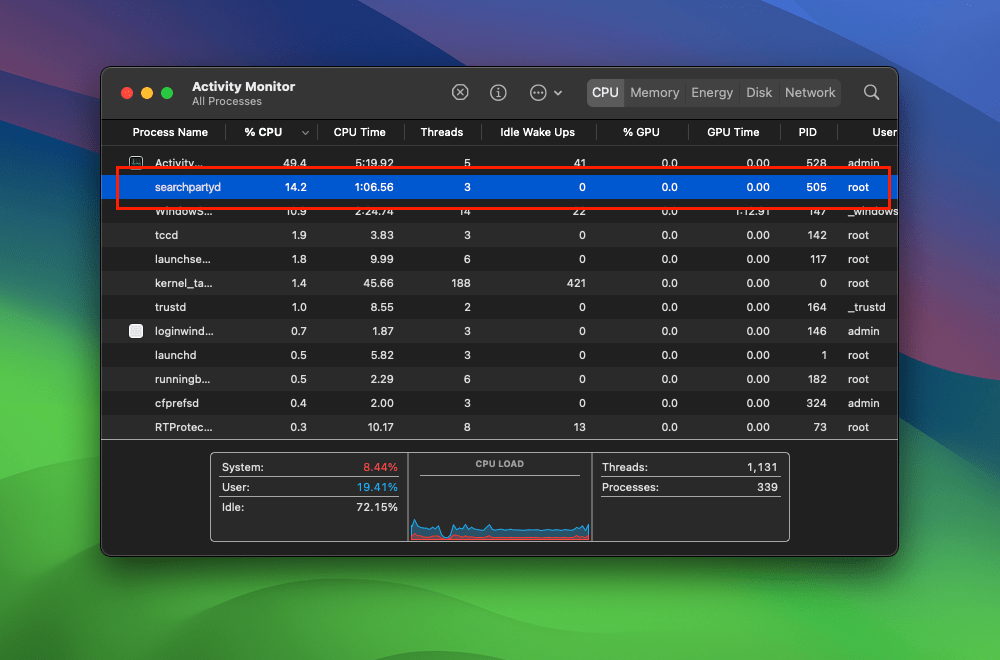
A frequently reported issue among macOS users is the high CPU usage associated with searchpartyd. This can lead to problems like overheating and rapid battery depletion. Despite some misconceptions, searchpartyd is not a form of malware or virus but an authentic and essential part of macOS. However, users have limited control over this process due to its protected status within the operating system. Tools like EtreCheck are invaluable in identifying applications that may be causing excessive CPU usage by searchpartyd.
exploring sshd-keygen-wrapper on Mac
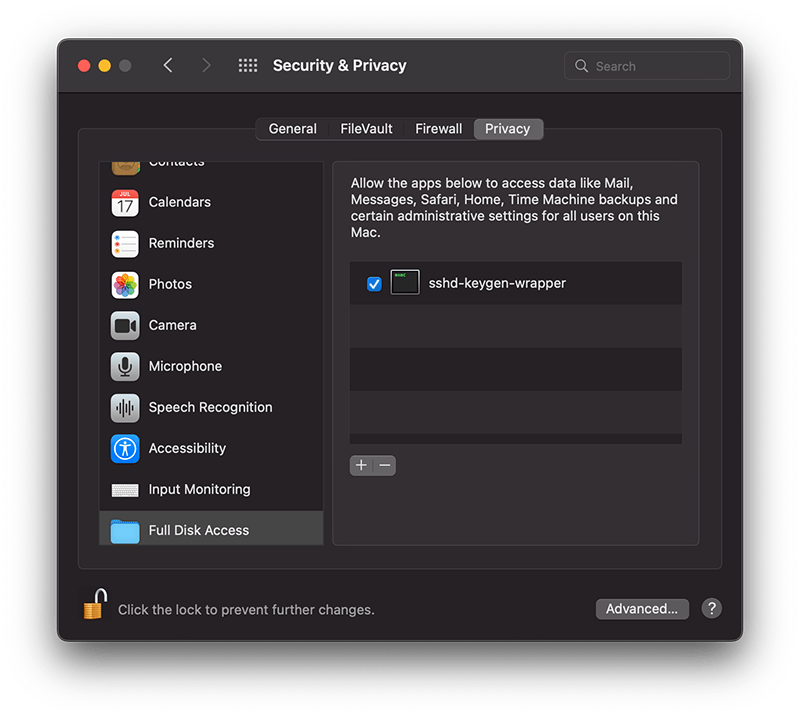
The sshd-keygen-wrapper tool, located within macOS Privacy settings, has garnered attention from users, particularly when they discover it in the Full Disk Access section of their Privacy preferences. While its presence might be disconcerting to some, a deeper understanding of its purpose and functionality can dispel any concerns.
The inclusion of sshd-keygen-wrapper in the Full Disk Access section can be perplexing. Some users may interpret it as an indication of a security compromise or malware. However, the reality is that sshd-keygen-wrapper is an integral component of macOS, functioning as an SSH secure shell key generator. Its primary role is to facilitate users in enabling or disabling remote access to their Mac via the Secure Shell Protocol (SSH).
The visibility of sshd-keygen-wrapper in Full Disk Access correlates with the Remote Login setting. Users who have never activated Remote Login will not encounter this tool. But for those who have, the tool will be present, albeit disabled by default, indicating that its access and permissions are inactive.
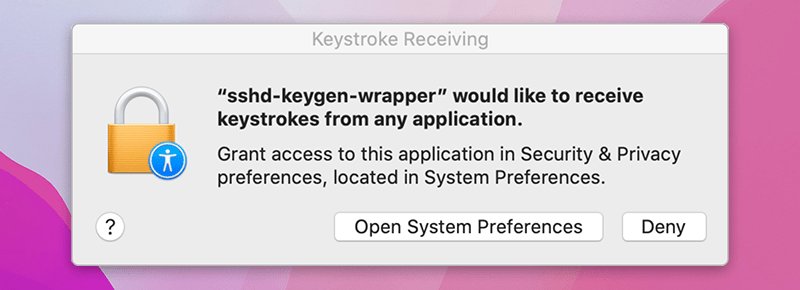
While navigating the Privacy settings on a Mac, users might come across a popup message stating, “‘sshd-keygen-wrapper’ would like to receive keystrokes from any application.” This message can be particularly perplexing, leading to concerns about the tool’s intentions and whether it poses any security risks.
Is it malware?
A prevalent misconception is associating sshd-keygen-wrapper with malware or unwanted software. Contrary to this belief, the tool is an authentic part of macOS and poses no malicious intent. Its placement in the Full Disk Access section is inherently tied to the SSH remote access feature. Activating SSH remote access from System Preferences ensures the association of sshd-keygen-wrapper, which then guarantees the generation of secure SSH shell keys for remote connections.
Should sshd-keygen-wrapper be granted Full Disk Access?
A frequently posed question revolves around whether sshd-keygen-wrapper should receive full disk access. Users contemplating remote access to their Mac via SSH might consider this option. By granting Full Disk Access to sshd-keygen-wrapper, macOS inherently extends the same privilege to SSH. As a result, any individual accessing the Mac through SSH can access all data, encompassing emails, messages, and files. The choice to activate this feature should stem from individual security assessments and requirements.